
-
Security Services
- Network Pentesting
- Application Pentesting
- Services on request
- Industry
- Publications
- About us
- Contact us
Many companies make use wireless (WiFi) networks, which are often the target of attacks because a successful attack on WiFi devices can provide direct access to the internal network.
While these networks bring many benefits, an unprotected or poorly configured network can lead to unauthorized use and possible security risks such as data leakage.
The wireless network (WiFi) penetration test/audit is designed to assess the security of your wireless network that may be compromised due to incorrect configuration or implementations.
The penetration test results in a report that contains the identified vulnerabilities that are assigned a risk and recommendations on how to remove them.
The penetration test can be performed using the BLACK BOX (no information about the tested environment), GRAY BOX (partial information about the test environment) or WHITE BOX (full information about the tested environment, including configuration files of devices / settings) method.
The cost of the penetration test depends on the depth of the tests, the size and complexity of the tested infrastructure. The price is determined after customer consultation, which determines the scope, type of test and other requirements from the customer.
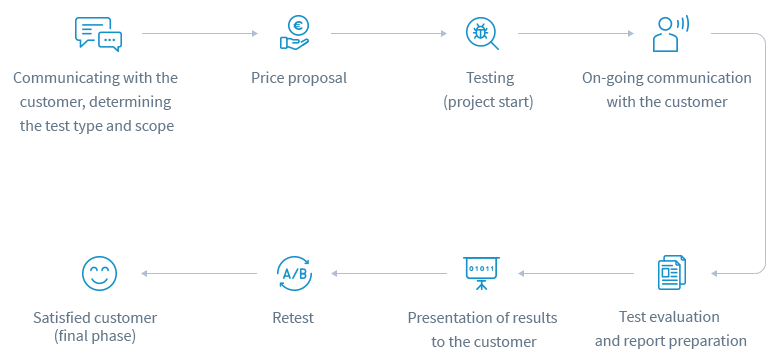

Communicating with the customer, determining the test type and scope
↓

Price proposal
↓

Testing(project start)
↓

On-going communication with the customer
↓

Test evaluation and report preparation
↓

Presentation of results to the customer
↓

Retest
↓

Satisfied customer (final phase)
For the penetration test, we use methodologies such as the Open Source Security Testing Methodology Manual (OSSTMM), NIST800-115, the Information Systems Security Assessment Framework (ISSAF), and especially our internally developed methodology that simulates a real attack. Our experts are holders of the Offensive Security Wireless Professional (OSWP) certification.
Penetration tests for wireless networks usually include:
If you are interested in this service or would like to know more,
please contact our expert who will be happy to help
you.